Keycloak is a key component of our Inalogy IAM solution. We are continuously reducing the gap between open-source and commercial IAM solutions from the perspective of user experience. Even though Keycloak provides Multi-Factor authentication via TOTP, it lacks super convenient push notifications. So, we decided to change that, and now Keycloak push notifications are a reality.
How Keycloak push notifications work
Keycloak has full native support for the TOTP second factor authentication. To extend Keycloak with push notifications capability was not a trivial task. We needed to establish a connection between the Keycloak instance and the mobile Authenticator application. To accomplish this, three components were needed, so Keycloak reaches your mobile phone and it replies with the OTP back to Keycloak.



Keycloak extension
We integrated push notifications seamlessly into the Keycloak authentication flow wizard via this extension. You can then easily modify your existing authentication flows by extending them with push notifications, even conditional ones. This allows you to request a second factor dynamically, based on the criticality of the requested access. Here is an example of how Keycloak push notification flow is conditioned by a specific role – havePush.
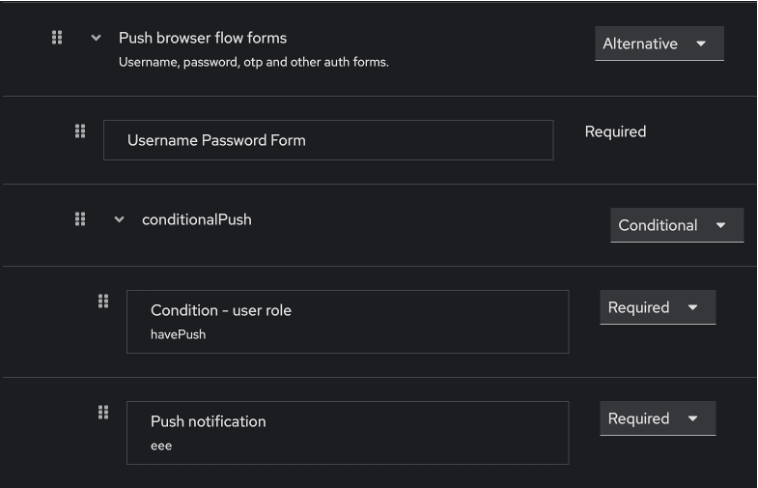
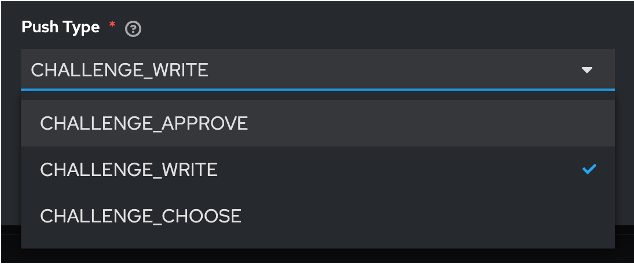
Users have the possibility to set up the type of MFA verification method based on the desired security level.
- Approve/Deny – The simplest option where the user clicks “Yes” or “No” (or “Approve” or “Deny”) to confirm their identity
- Number Matching – Where the user selects the correct number from multiple options that match what’s shown on their login screen
- Number Challenge-Response – Where the user enters a number displayed on their login screen into the authentication app
Inalogy Messaging Service
Alternatively, IMS will create a bridge between Keycloak and the iOS or Android mobile interface on the other side. It’s an online service provided by Inalgy that integrates Keylock push notifications requests with Apple notification service (APNS) and Firebase Cloud Messaging for Android devices. IMS is designed as multitenant and is capable of managing multiple organizations.
The advantage of the IMS service is its universality. It can provide an integration interface for Keycloak and any other identity provider that lacks push notification support. You need to create an extension on your IDP to communicate with IMS, and we will take care of the rest.
Inalogy authenticator
The final component of the solution is Inalogy Authenticator. We have developed a user-friendly, fully capable MFA application. It is a native application for both iOS and Android and can be downloaded directly from the Apple App Store or the Google Play Store.
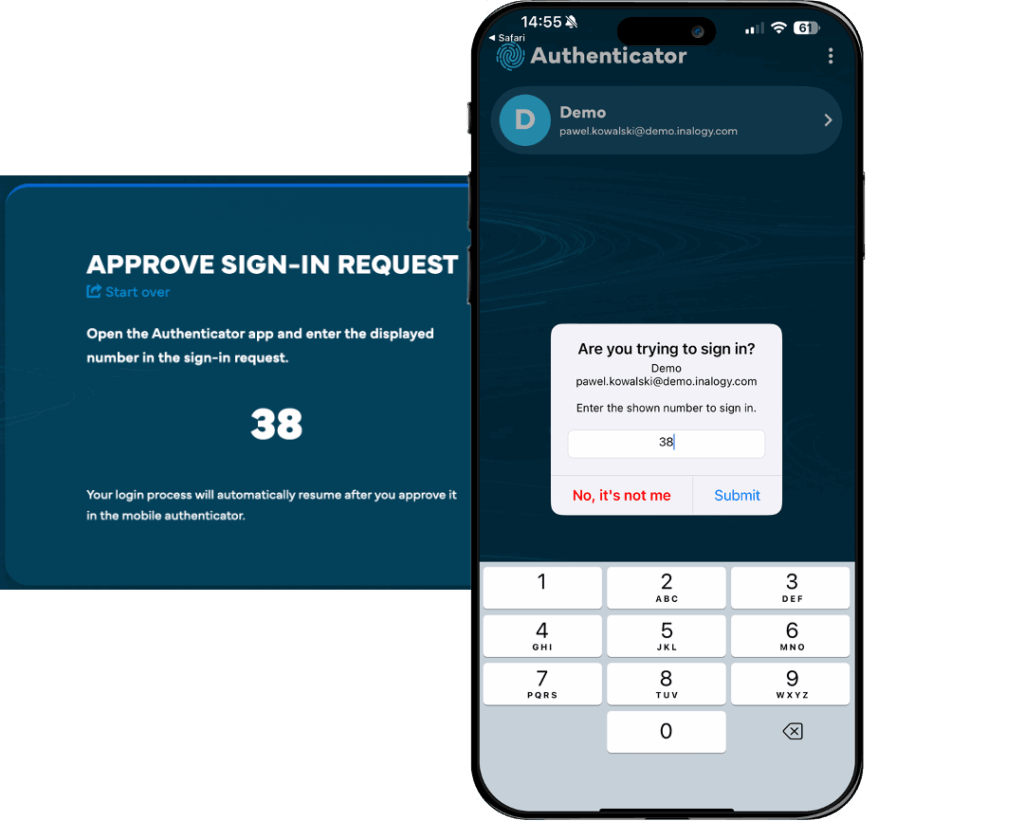
When a request reaches your device, you will be asked to confirm according to the security level configured in the authentication flow. Once you confirm your authentication request on your device, the authentication flow in Keycloak will automatically proceed through the MFA step.
Conclusion
Open-source tools are great and getting better every day. However, they often provide isolated services and feel like they are not part of the larger ecosystem. We want our customers to have this very cost-effective solution without feeling that they are connected to additional discomfort. MidPoint and Keycloak, with their mutual integration, are cornerstones of our IAM solution, and with Keycloak push notifications MFA, open-source solutions are pushed closer to the user.
Want to read more ?

